Enterprise Endpoint Security – Rules to Protect from Advanced Malware and Security Breaches – Xorlogics

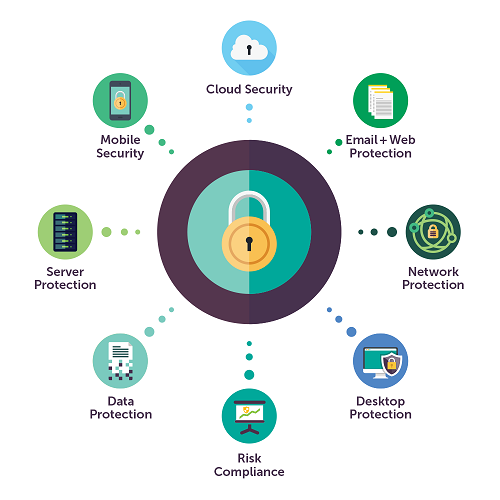
Protected endpoint applications provide common security posture for enterprise cloud ecosystems | Dave Waterson on Security

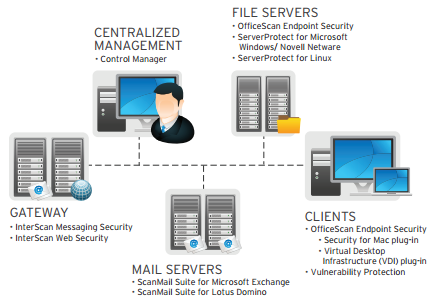
Trend Micro Enterprise Security f/Endpoints Light, 12m, 101-250u, Ren EN00204392 Data Sheet - Page 1 of 2 | Manualsbrain.com